How To SSH Remote IoT Raspberry Pi (Free Download For Windows)
Can you securely access and control your Raspberry Pi-powered IoT device from anywhere, without spending a dime or wrestling with complex configurations? The ability to remotely manage your Raspberry Pi, especially in the context of IoT, is not just a convenience; it's a fundamental necessity for efficient development, monitoring, and troubleshooting, particularly when dealing with geographically dispersed devices.
The quest for a free, reliable method to establish an SSH (Secure Shell) connection to your Raspberry Pi, especially from a Windows environment, is a common one among developers, hobbyists, and professionals alike. SSH provides a secure channel for remote command execution, file transfer, and more, forming the bedrock of remote device management. While the concept is straightforward, the implementation often presents challenges related to network configurations, firewalls, and the intricacies of setting up secure tunnels. This article aims to demystify this process, offering a comprehensive guide to setting up a free and secure SSH connection to your Raspberry Pi from a Windows machine.
Before diving in, let's address the elephant in the room: the "free download windows" aspect. This refers to utilizing free software tools on your Windows machine to facilitate the SSH connection. There are no subscription fees or hidden costs associated with the methods described below.
We'll explore the essential components, step-by-step configuration procedures, and some best practices for securing your connection, ensuring your IoT device remains protected from unauthorized access. The focus will be on practicality, enabling you to get your system up and running quickly and efficiently.
Understanding the Core Components: SSH, Raspberry Pi, and Windows
At the heart of this setup are three key components: SSH, your Raspberry Pi, and your Windows machine. SSH is the secure protocol, the Raspberry Pi is your remote IoT device, and your Windows machine is the control center. Let's break down each one.
SSH (Secure Shell): SSH is a network protocol that provides a secure channel for communication between two devices. It encrypts the traffic, ensuring that data transmitted over the connection remains confidential. This is crucial when dealing with remote devices, especially when youre transmitting sensitive information or executing commands that could potentially compromise the device if intercepted. SSH uses a client-server model, where the client initiates the connection and the server (in this case, your Raspberry Pi) responds.
Raspberry Pi: The Raspberry Pi is a low-cost, credit-card-sized computer that has gained immense popularity in the IoT world. Its affordability, versatility, and ease of use make it an ideal platform for a wide range of projects, from home automation to data logging and environmental monitoring. The Raspberry Pi typically runs a Linux-based operating system, such as Raspbian, which includes an SSH server by default. This built-in SSH server makes remote access relatively straightforward.
Windows Machine: Your Windows machine acts as the client, from which youll initiate the SSH connection to your Raspberry Pi. Youll need an SSH client installed on your Windows machine to establish the connection. Fortunately, several free and excellent SSH clients are available for Windows, and we'll explore one of the most popular options later.
Setting Up the Raspberry Pi
The first step involves preparing your Raspberry Pi for remote access. This includes ensuring it's connected to your network (either via Ethernet or Wi-Fi) and enabling SSH on the device. Here's a breakdown:
1. Powering Up and Connecting: Plug in your Raspberry Pi and connect it to your network. Ensure its connected to a power source and that it has an active internet connection. If youre using Wi-Fi, youll need to configure the Wi-Fi settings during the initial setup or through the Raspberry Pi's configuration utility.
2. Enabling SSH: The Raspbian operating system typically has SSH disabled by default for security reasons. Youll need to enable it to allow remote access. There are a few ways to achieve this:
a. Using the Raspberry Pi Configuration Tool: This is the easiest method, especially if you have a monitor, keyboard, and mouse connected to your Raspberry Pi. Boot up the Raspberry Pi and open the terminal. Type `sudo raspi-config` and press Enter. Navigate to "Interface Options," then select "SSH." Choose "Enable" when prompted.
b. Enabling SSH via SD Card Configuration (Headless Setup): If you don't have a monitor, keyboard, or mouse connected to your Pi (a "headless" setup), you can enable SSH by creating an empty file named `ssh` (without any file extension) in the root directory of your Raspberry Pi's SD card. This file acts as a trigger, instructing the system to enable SSH on the first boot. You can create this file on another computer (like your Windows machine) after flashing the Raspbian image onto the SD card.
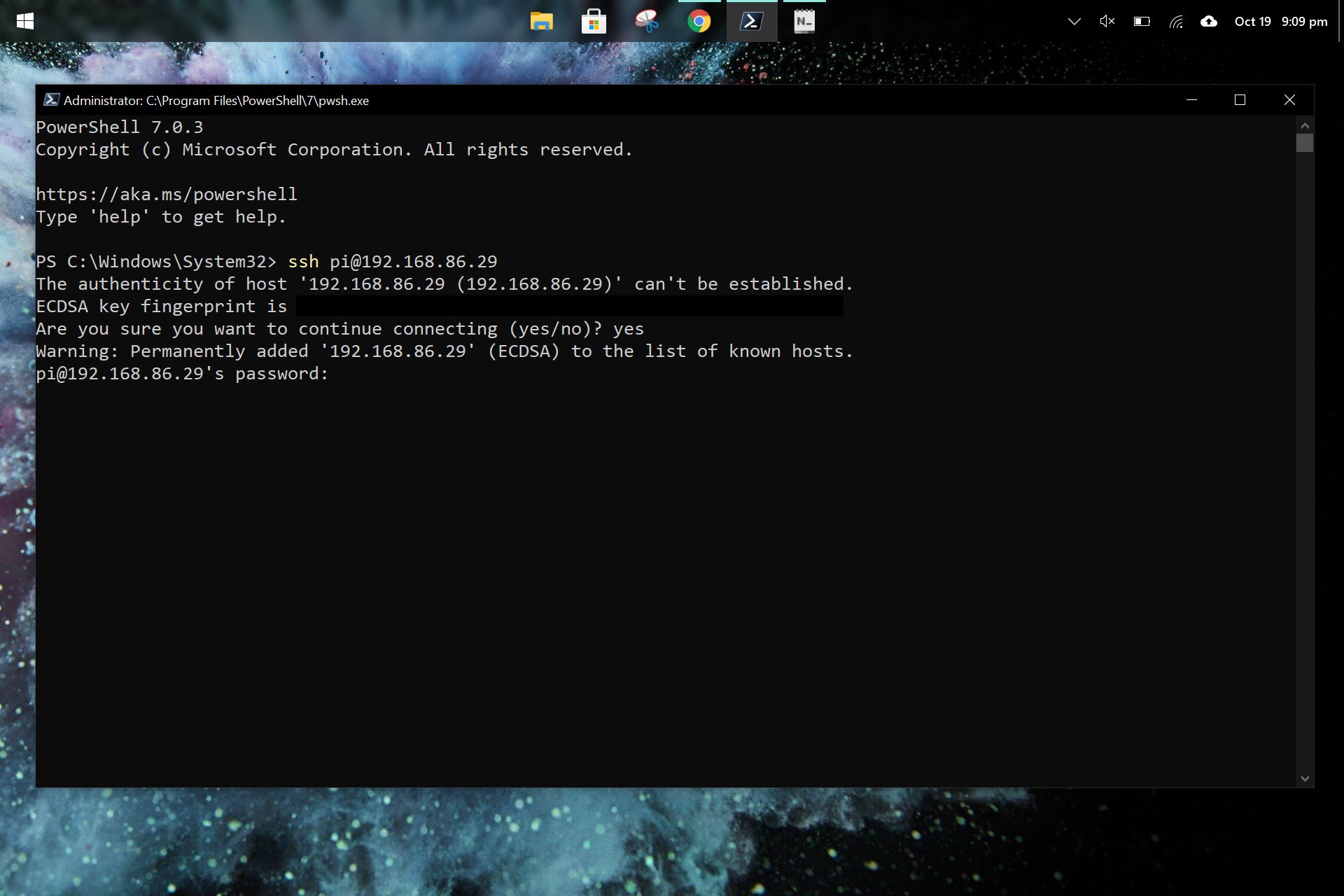
3. Finding Your Raspberry Pi's IP Address: You'll need the IP address of your Raspberry Pi to connect to it from your Windows machine. There are several ways to find this:
a. From the Raspberry Pi's Terminal: If you have a monitor connected, open the terminal and type `hostname -I`. This will display the IP address of your Pi.
b. From Your Router: Log in to your router's administration panel (usually by typing the router's IP address into your web browser). Look for a list of connected devices. Your Raspberry Pi should be listed there, along with its IP address.
c. Using an IP Scanner: There are numerous free IP scanner tools available for Windows that can scan your network and identify connected devices, including their IP addresses.
Setting Up Your Windows Machine
With your Raspberry Pi configured and connected to the network, its time to set up your Windows machine to connect to it via SSH.
1. Downloading and Installing an SSH Client: The most popular and user-friendly SSH client for Windows is PuTTY. It's free, lightweight, and widely used. You can download it from a trusted source like the official PuTTY website.
a. Go to the PuTTY website and download the appropriate installer for your version of Windows (32-bit or 64-bit).
b. Run the installer and follow the on-screen instructions to install PuTTY.
2. Connecting to Your Raspberry Pi using PuTTY:
a. Open PuTTY. You'll see a configuration window.
b. In the "Host Name (or IP address)" field, enter the IP address of your Raspberry Pi (the one you found earlier).
c. The default port for SSH is 22. Ensure the "Port" field is set to 22.
d. Under "Connection type," select "SSH."
e. Click "Open."
f. If this is your first time connecting to the Raspberry Pi, you might see a security alert asking you to accept the host key. Click "Yes" to proceed.
g. You'll be prompted for your username and password. The default username for Raspbian is usually "pi," and the default password is "raspberry" (unless you've changed it). Enter these credentials.
h. Once you've entered your credentials correctly, you should be logged in to your Raspberry Pi's terminal. You can now execute commands remotely.
Securing Your SSH Connection
While the setup described above provides remote access, it's essential to secure your SSH connection to protect your device from unauthorized access. Here are some important security measures:
1. Changing the Default Password: The default password "raspberry" is a major security vulnerability. Immediately change the default password to a strong, unique password. You can do this through the Raspberry Pi's terminal using the `passwd` command.
2. Creating a Strong Password: Your new password should be at least 12 characters long and include a combination of uppercase and lowercase letters, numbers, and special characters. Avoid using easily guessable information like birthdays or common words.
3. Disabling Password Authentication (and using SSH Keys): Password authentication is inherently vulnerable to brute-force attacks. A more secure approach is to disable password authentication and use SSH keys. This involves generating a key pair (a private key and a public key). The private key is kept on your Windows machine, and the public key is placed on your Raspberry Pi. When you connect, the SSH client uses the private key to prove your identity, eliminating the need for a password.
a. Generating SSH Keys on Windows (using PuTTYgen): PuTTY comes with a tool called PuTTYgen for generating SSH keys. Open PuTTYgen, select "RSA" or "ED25519" for the key type, and click "Generate." Move your mouse around in the blank area to generate randomness for the key. Once the key is generated, copy the contents of the "Public key for pasting into authorized keys file" field.
b. Adding the Public Key to Your Raspberry Pi: SSH into your Raspberry Pi using your current password. Open the `authorized_keys` file in the `.ssh` directory. If the `.ssh` directory doesn't exist, create it (e.g., `mkdir ~/.ssh`). Then, use a text editor (like `nano`) to open the `authorized_keys` file (e.g., `nano ~/.ssh/authorized_keys`). Paste the public key you copied from PuTTYgen into this file. Save the file.
c. Configuring PuTTY to use the Private Key: In PuTTY's configuration window, go to "Connection" -> "SSH" -> "Auth." Click "Browse" and select the private key file (.ppk) you saved from PuTTYgen.
d. Disabling Password Authentication on the Raspberry Pi: (This is optional, but highly recommended once you've confirmed key-based authentication works.) Edit the SSH configuration file on your Raspberry Pi (using `sudo nano /etc/ssh/sshd_config`). Find the lines `#PasswordAuthentication yes` and `#PubkeyAuthentication yes`. Uncomment and modify them as follows: `PasswordAuthentication no` and `PubkeyAuthentication yes`. Save the file and restart the SSH service (`sudo systemctl restart ssh`). After this change, only SSH key authentication will be allowed, significantly enhancing security.
4. Changing the Default SSH Port (Security Through Obscurity): While not a primary security measure, changing the default SSH port (port 22) can deter automated attacks. You can change the port in the `/etc/ssh/sshd_config` file (using `sudo nano /etc/ssh/sshd_config`). Find the line `#Port 22` and change it to a different port number (e.g., `Port 2222`). Save the file and restart the SSH service.
Important: When you change the port, remember to specify the new port number when connecting to your Raspberry Pi using PuTTY (in the "Port" field of the configuration window).
5. Using a Firewall (UFW): Consider enabling the Uncomplicated Firewall (UFW) on your Raspberry Pi. UFW provides a simple way to manage firewall rules and control network traffic. This is especially useful if your Raspberry Pi is connected to the internet. Install UFW with `sudo apt-get update && sudo apt-get install ufw`. Enable it with `sudo ufw enable` and set rules to allow SSH access on your chosen port (e.g., `sudo ufw allow 22` or `sudo ufw allow 2222` if you changed the port). Remember to allow the new SSH port before you enable the firewall, or you'll be locked out.
6. Regular Updates: Keep your Raspberry Pi's operating system and software packages updated. Regularly update the system using `sudo apt update` and `sudo apt upgrade`. This ensures you have the latest security patches and bug fixes.
7. Monitoring Logs: Regularly check the SSH logs on your Raspberry Pi for suspicious activity. The SSH logs are typically located in `/var/log/auth.log` or `/var/log/secure`. You can examine these logs to identify failed login attempts, unusual activity, or other potential security breaches.
Addressing Common Issues
While setting up SSH is usually straightforward, you might encounter some issues. Here are some common problems and their solutions:
1. Connection Refused: If you can't connect, the most likely causes are:
a. Incorrect IP Address: Double-check that you're using the correct IP address of your Raspberry Pi.
b. SSH Not Enabled: Ensure SSH is enabled on your Raspberry Pi (as described earlier).
c. Firewall Issues: Your Windows firewall or a firewall on your network might be blocking the connection. Temporarily disable your Windows firewall (for testing purposes only) or add an exception for PuTTY (in the Windows Firewall settings) to allow incoming connections on port 22 (or your custom SSH port).
d. Raspberry Pi Not Connected to the Network: Verify that your Raspberry Pi is connected to the network and has an active internet connection.
e. SSH Service Not Running: The SSH service might not be running on your Raspberry Pi. Try restarting it with `sudo systemctl restart ssh` on the Pi.
2. Authentication Failed:
a. Incorrect Username/Password: Double-check that you're entering the correct username and password (or that your SSH key authentication is correctly configured).
b. Keyboard Layout Issues: If you're using a different keyboard layout on your Raspberry Pi than on your Windows machine, it could lead to incorrect password entry. Ensure you're using the correct keyboard layout when entering your password.
3. Network Configuration Problems:
a. Router Configuration: If you're trying to access your Raspberry Pi from outside your local network (e.g., from the internet), you'll need to configure port forwarding on your router. This involves forwarding traffic on port 22 (or your custom SSH port) to the internal IP address of your Raspberry Pi. Consult your router's documentation for specific instructions.
b. Dynamic IP Address: If your internet service provider (ISP) assigns you a dynamic IP address, your IP address might change periodically. This means youll need to update your connection settings (in PuTTY) whenever your IP address changes. Consider using a Dynamic DNS (DDNS) service, which provides a hostname that automatically updates with your IP address. There are many free DDNS providers available.
4. PuTTY Not Responding/Freezing:
a. Network Issues: Verify your internet connection. A poor connection can cause delays or disconnections.
b. Raspberry Pi Overloaded: If your Raspberry Pi is under heavy load (e.g., running intensive processes), it might be unresponsive. Try connecting again later, or consider optimizing the processes running on the Pi.
c. Firewall Blocking the Connection: Ensure your firewall isn't blocking the connection (as mentioned earlier).
Advanced Techniques and Considerations
Once you have a basic SSH connection set up, you can explore more advanced techniques to enhance your workflow and security:
1. SSH Tunneling (Port Forwarding): SSH tunneling allows you to create secure connections to other services running on your Raspberry Pi (or on other devices accessible from your Raspberry Pi). This is useful for accessing web servers, databases, or other services that are not directly exposed to the internet.
a. Local Port Forwarding: Forward a port on your local machine to a port on the Raspberry Pi. For example, to access a web server running on port 80 on your Raspberry Pi, you could forward port 8080 on your Windows machine to port 80 on your Raspberry Pi. In PuTTY, go to "Connection" -> "SSH" -> "Tunnels" and add a new forwarded port (e.g., source port 8080, destination `localhost:80`).
b. Remote Port Forwarding: Forward a port on the Raspberry Pi to a port on your local machine (or another machine accessible from your local network). This is useful for accessing services that run on the remote machine (e.g., a database server) from your local machine.
2. Using a Reverse Proxy (e.g., Nginx): If you want to host multiple web applications on your Raspberry Pi, a reverse proxy can simplify the configuration and enhance security. Nginx is a popular choice. You can configure Nginx to listen on port 80 or 443 and forward traffic to different applications based on the domain name or path.
3. Automating SSH Connections (using scripts): For frequently used connections, you can automate the SSH login process using scripts. This can save time and reduce the risk of errors. For example, you can create a batch file (.bat) in Windows that launches PuTTY with the necessary connection settings.
4. Considerations for IoT Security:
a. Least Privilege Principle: Grant your Raspberry Pi user accounts only the minimum necessary permissions. Avoid running applications as root unless absolutely necessary.
b. Regular Audits: Periodically review the security settings on your Raspberry Pi and the network configuration to ensure that they are still secure.
c. Physical Security: If your Raspberry Pi is physically accessible, consider securing it to prevent unauthorized access.
d. Device Hardening: Disable unused services and ports on your Raspberry Pi to reduce the attack surface.
Conclusion
In summary, establishing a free and secure SSH connection to your Raspberry Pi from a Windows machine is a valuable skill for IoT development, maintenance, and troubleshooting. By following the steps outlined in this guide, you can securely access and control your devices remotely, regardless of your location, without incurring any financial costs. Remember to prioritize security by changing default passwords, using SSH keys, enabling firewalls, and regularly updating your system. With the knowledge and tools provided, you can confidently manage your Raspberry Pi-based IoT projects from the comfort of your Windows machine.