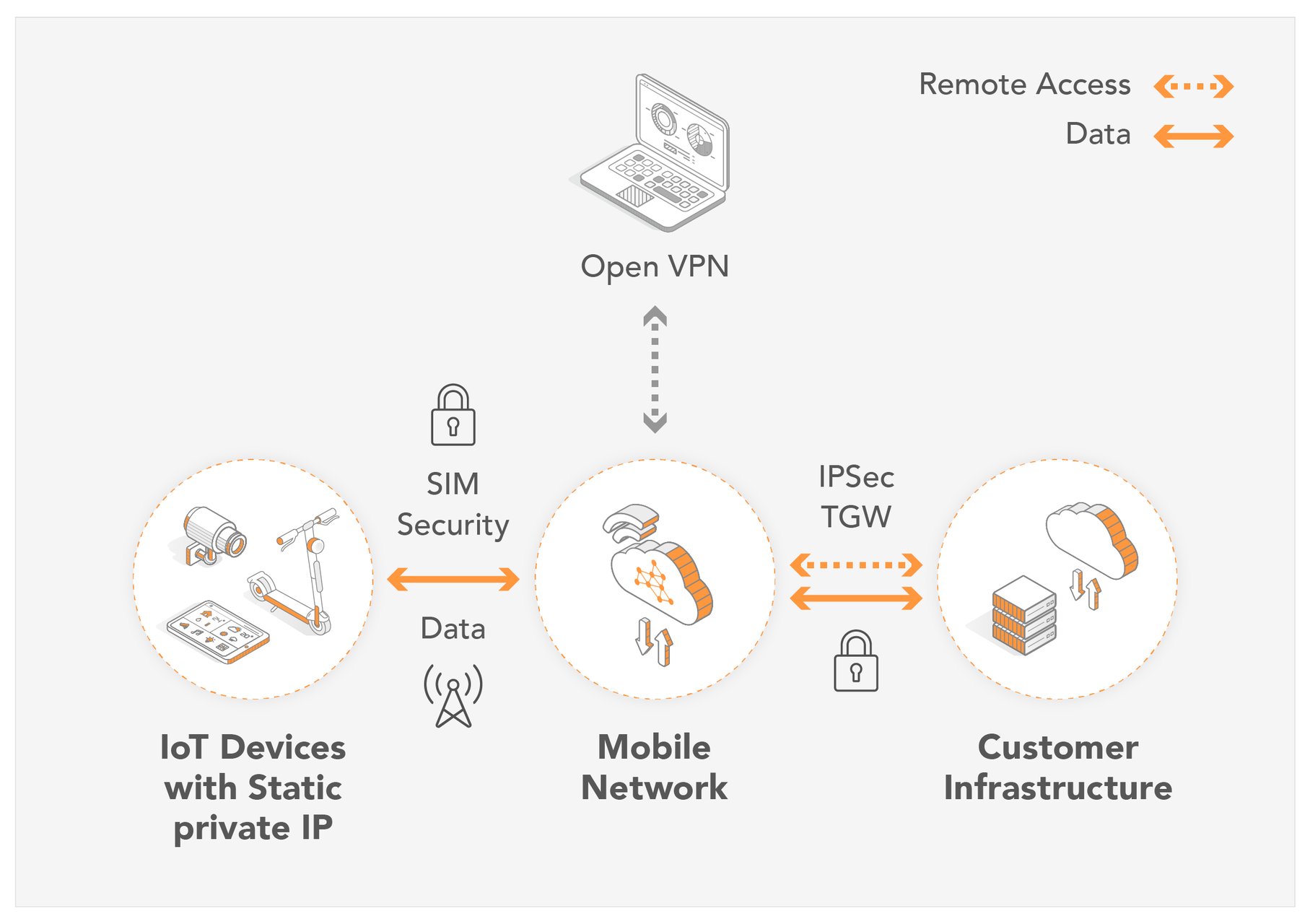
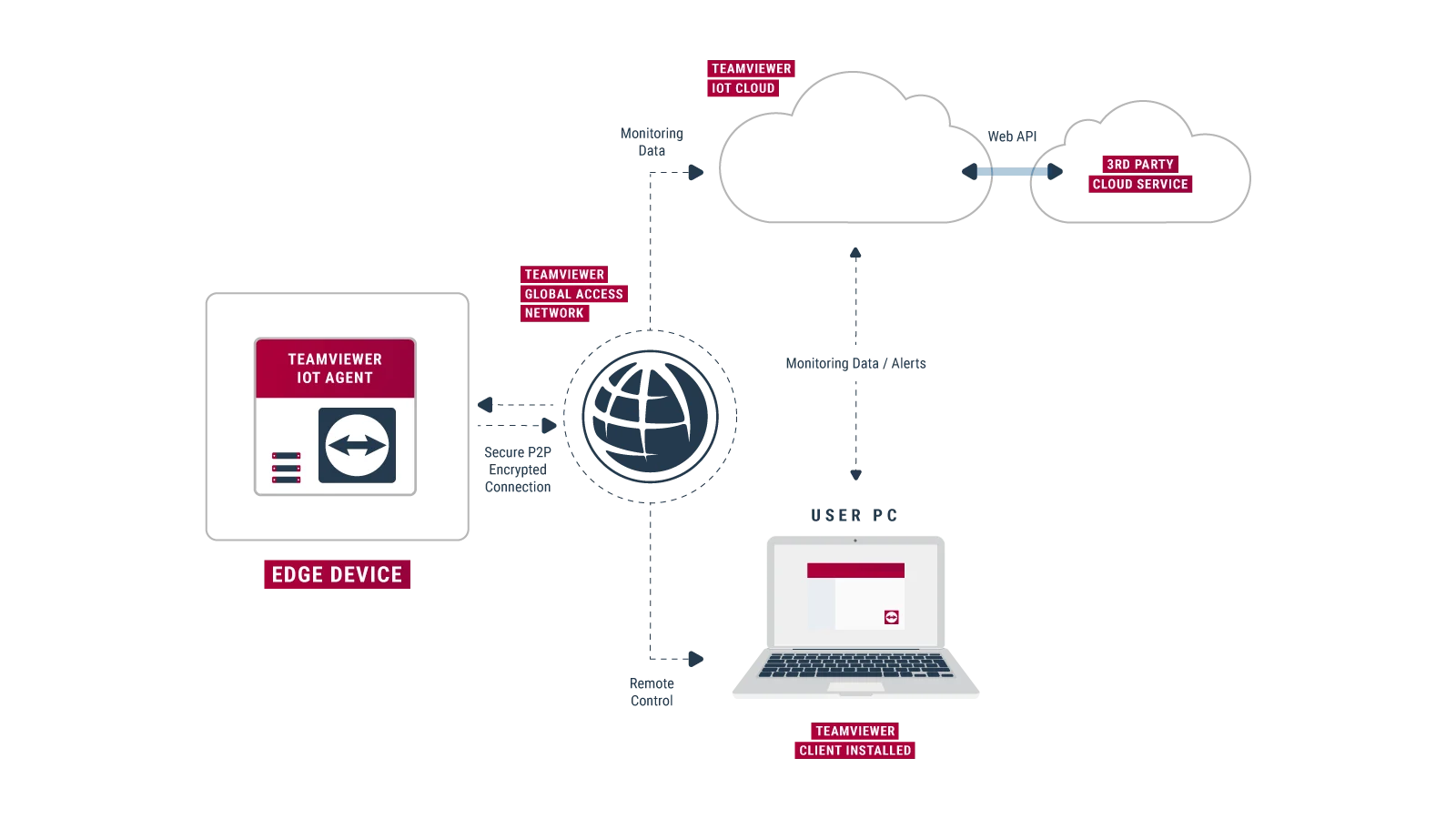
Remote Access Iot Behind
Is the Internet of Things (IoT) truly secure when we consider the realities of "remote access IoT behind"? The answer, often obscured by the rapid expansion of connected devices, is a resounding, and concerning, "no." This vulnerability is not just a theoretical possibility; it's a pervasive threat landscape that demands immediate and comprehensive attention. The promise of a hyper-connected world, where devices seamlessly communicate and automate tasks, is shadowed by the persistent risk of unauthorized access and malicious exploitation. The very convenience that defines the IoT its accessibility and remote control capabilities simultaneously creates a pathway for adversaries to infiltrate and compromise systems.
The challenge lies in the decentralized nature of the IoT ecosystem. Millions, even billions, of devices, from smart thermostats and refrigerators to industrial sensors and medical devices, are deployed across the globe. Each device represents a potential point of entry. Many are designed with minimal security protocols due to cost constraints or a focus on functionality, making them easy targets. Furthermore, the diversity of manufacturers, operating systems, and communication protocols creates a fragmented security landscape. Standardizing security practices across this sprawling network is a monumental task, and the consequences of failure are far-reaching.
Consider the implications for critical infrastructure. Power grids, water treatment plants, and transportation systems are increasingly reliant on IoT devices for monitoring and control. A successful cyberattack on these systems could have catastrophic consequences, disrupting essential services and endangering public safety. The financial implications are equally significant. Data breaches, intellectual property theft, and reputational damage can cripple businesses. The cost of remediation, legal fees, and lost revenue can be staggering. The rise of ransomware, specifically targeting IoT devices, has further amplified the threat. Attackers can lock down devices and demand hefty ransoms for their release, holding entire operations hostage.
The fundamental issue stems from the fact that "remote access IoT behind" presents a perfect storm for exploitation. The remote nature of these devices means they can be accessed from anywhere in the world. The lack of robust security measures leaves them vulnerable to a variety of attack vectors, including: weak passwords, unpatched vulnerabilities, insecure network configurations, and malware infections. Attackers can use these vulnerabilities to gain control of devices, steal sensitive data, or use the devices as a launchpad for further attacks. This can include creating botnets, which can be used to launch Distributed Denial of Service (DDoS) attacks or to mine cryptocurrencies.
The sophistication of attacks is also increasing. Attackers are constantly refining their techniques, utilizing artificial intelligence (AI) and machine learning (ML) to automate and optimize their attacks. They are also targeting the supply chain, compromising devices before they even reach the end user. This makes it even more difficult to detect and mitigate threats. The need for proactive security measures is more critical than ever, and the traditional reactive approach to cybersecurity is no longer sufficient. A shift towards a 'security by design' approach is essential, where security is embedded into the entire lifecycle of the device, from development to deployment and maintenance.
Let's delve into the specific components that make "remote access IoT behind" such a challenging problem. First, the attack surface is vast. Every connected device, regardless of its function, presents a potential point of entry. From smart home appliances to industrial control systems, each device operates on a network and has an IP address, making it accessible from the internet. This accessibility, while offering convenience and control, is also the gateway for malicious actors.
Secondly, the lack of standardization is a major obstacle. Unlike personal computers or smartphones, the IoT ecosystem is highly fragmented. There is a vast array of manufacturers, operating systems, and communication protocols, resulting in a lack of interoperability and consistency in security practices. This fragmentation makes it challenging to implement and enforce uniform security standards across the entire IoT landscape.
Thirdly, the resource constraints on many IoT devices make robust security implementation difficult. Many devices are designed to be low-cost and energy-efficient, which often necessitates compromises in security. This can mean using weaker encryption algorithms, limited processing power for security functions, and fewer resources for patching vulnerabilities. Resource-constrained devices are therefore more susceptible to exploitation.
The prevalence of outdated software and unpatched vulnerabilities is another critical factor. Many IoT devices are deployed with software that is never updated, or updates are infrequent and difficult to implement. This creates a situation where known vulnerabilities are left unaddressed, making the devices easy targets for attackers. The lack of vendor support for older devices further exacerbates this problem. When vendors discontinue support, they no longer provide security patches, leaving the devices vulnerable for the remainder of their lifespan.
Moreover, the user behavior can also introduce significant security risks. Many users are not aware of the security risks associated with IoT devices. They often use weak passwords, fail to change default settings, and do not keep their devices updated. They may also unwittingly install malicious apps or visit phishing websites, further exposing their devices to compromise. Improving user awareness and promoting best practices is essential for improving the overall security posture of the IoT ecosystem.
Consider the implications of these vulnerabilities in practical scenarios. Imagine a smart home where an attacker gains access to the thermostat. They could adjust the temperature, causing discomfort or damage. Or, they might access the security cameras, monitoring the home's occupants and gaining intelligence for future attacks. In a factory setting, compromised sensors could provide false data, leading to production errors or even physical damage. In the healthcare sector, a compromised medical device could put a patient's life at risk. The potential for harm is vast and varied.
A key component in this complex landscape is the cloud, where many IoT devices send their data. The cloud infrastructure is often the central point of control and management for these devices, making it a prime target for attackers. A successful compromise of the cloud platform could expose the data from millions of devices, as well as provide access to the devices themselves. Therefore, the security of the cloud platform is of utmost importance to the overall security of the IoT ecosystem. Secure cloud practices, including robust authentication, access controls, and data encryption, are essential.
In response to these challenges, a multi-faceted approach to security is necessary. This approach must involve manufacturers, developers, users, and regulators. Here are some key recommendations:
- Security by Design: Manufacturers should prioritize security from the outset, incorporating security features into the design, development, and testing phases of devices.
- Strong Authentication: Multi-factor authentication should be implemented on all devices and cloud platforms. Strong passwords are the first line of defense.
- Regular Updates and Patch Management: Devices should be regularly updated with security patches to address known vulnerabilities. Automatic update mechanisms can simplify this process.
- Network Segmentation: Segmenting the IoT network from other networks can limit the impact of a breach.
- Data Encryption: Data should be encrypted both in transit and at rest to protect it from unauthorized access.
- User Education: Users should be educated about the security risks associated with IoT devices and best practices for securing them.
- Vulnerability Scanning and Penetration Testing: Regular security assessments should be conducted to identify and address vulnerabilities.
- Security Standards and Regulations: Industry-wide security standards and regulations are needed to ensure that all IoT devices meet a minimum level of security.
- Incident Response Plan: Organizations and individuals should have an incident response plan in place to address security breaches.
- Supply Chain Security: Security measures should be implemented throughout the supply chain to ensure that devices are secure from the point of manufacture to deployment.
The challenge of securing "remote access IoT behind" requires collaborative effort. The development and implementation of security standards, best practices, and regulations are essential for improving the security of the IoT ecosystem. By implementing the recommendations outlined above, the risk of unauthorized access and malicious exploitation can be significantly reduced. Security cannot be an afterthought, it must be a fundamental consideration throughout the entire lifecycle of IoT devices. The future of the IoT, and the benefits it promises, depend on the commitment to securing the "remote access IoT behind." Ignoring this responsibility will ultimately jeopardize the promise of a connected, secure, and beneficial future.
Consider this scenario: a smart city, with its array of interconnected sensors, traffic management systems, and surveillance cameras, is targeted in a coordinated cyberattack. The attackers remotely access the traffic lights, causing widespread gridlock and chaos. They disable the surveillance cameras, providing cover for other malicious activities. They even gain access to the water treatment plant, potentially disrupting water supply. This is not a futuristic fantasy; it's a potential reality if adequate security measures are not implemented.
The evolution of hacking techniques also contributes to the growing threat. Attackers are employing increasingly sophisticated methods, including: AI-powered attacks that can automatically identify and exploit vulnerabilities, supply chain attacks that target devices before they reach the end user, and zero-day exploits that take advantage of previously unknown vulnerabilities. These advanced techniques require a proactive and adaptive security approach.
The legal and regulatory landscapes are also evolving in response to the growing security threats. Governments around the world are enacting new laws and regulations to address IoT security concerns, including data privacy and security standards. These regulations place greater responsibility on manufacturers and businesses to implement robust security measures and protect user data. Compliance with these regulations is crucial, not only to avoid legal penalties but also to build trust with consumers.
To ensure the long-term security and viability of the IoT, a comprehensive, multi-layered approach is required. This approach involves the following key elements:
- Risk Assessment: Identify and assess potential security risks and vulnerabilities.
- Security Architecture: Design and implement a secure network architecture, including network segmentation and access controls.
- Device Hardening: Secure the individual devices by implementing strong passwords, disabling unnecessary features, and keeping the firmware up-to-date.
- Data Protection: Encrypt data in transit and at rest, and implement data loss prevention measures.
- Identity and Access Management (IAM): Implement strong authentication and authorization mechanisms to control access to devices and data.
- Security Monitoring and Incident Response: Implement security monitoring systems to detect and respond to security incidents.
- Supply Chain Security: Secure the supply chain to prevent the introduction of malicious devices or components.
- Collaboration and Information Sharing: Collaborate with industry peers and security experts to share threat intelligence and best practices.
- Continuous Improvement: Continuously monitor, evaluate, and improve security measures.
The challenges and risks associated with "remote access IoT behind" are significant, but they are not insurmountable. By adopting a proactive, multi-faceted approach to security, we can mitigate the risks and unlock the full potential of the Internet of Things. The key is a commitment to security, a culture of vigilance, and a willingness to adapt to the ever-evolving threat landscape.