How To SSH Into Your IoT Device On AWS + Tips
Is securing your Internet of Things (IoT) devices in the cloud a constant source of anxiety? The ability to securely access and manage your IoT devices remotely via SSH to AWS is not just a convenience, its a fundamental necessity for maintaining device integrity, ensuring data security, and enabling efficient troubleshooting and updates. The integration of SSH with Amazon Web Services (AWS) provides a robust and scalable solution for managing a diverse array of IoT devices, from simple sensors to complex industrial equipment. This article delves into the practical aspects, security considerations, and best practices for establishing and maintaining secure SSH connections to your IoT devices hosted within the AWS ecosystem.
The allure of IoT lies in its promise of connecting physical objects to the digital realm, creating a network of intelligent devices that can collect, analyze, and exchange data. However, this interconnectedness introduces significant security challenges. Every IoT device becomes a potential entry point for malicious actors, making the security of these devices paramount. SSH, or Secure Shell, is a cryptographic network protocol that allows for secure communication between devices over an unsecured network. When combined with AWS, SSH provides a powerful mechanism for remotely accessing and managing IoT devices, offering a secure channel for transferring data, executing commands, and performing system maintenance. Securing this SSH connection is essential for protecting your devices and the data they generate.
Let's first understand the context: Imagine a world where thousands of sensors are deployed across a vast geographical area, constantly collecting environmental data. Without a secure and reliable method to access and manage these devices, any attempt to update their firmware, diagnose operational issues, or retrieve critical data becomes a herculean task. Furthermore, the potential for unauthorized access and manipulation poses a severe risk. This is where the power of SSH to IoT devices hosted on AWS truly shines. SSH acts as a secure tunnel, protecting the communication between your management workstation and the IoT devices. This secure channel ensures that sensitive data is protected from eavesdropping and tampering, and enables you to maintain operational control over your IoT infrastructure.
The core advantage of using SSH for IoT device management in AWS lies in its inherent security features. SSH employs strong encryption algorithms to protect data in transit. Furthermore, SSH allows for the implementation of robust authentication mechanisms, such as key-based authentication, which eliminates the need for password-based logins, thereby significantly reducing the risk of brute-force attacks and unauthorized access. AWS provides a wealth of tools and services that can be used to further enhance the security of SSH connections, including security groups, network ACLs, and AWS Identity and Access Management (IAM).
Consider the practical scenario of deploying an IoT device that is responsible for monitoring water quality in a remote location. This device is powered by a small embedded system running a customized operating system. Periodically, the device needs to be updated with the latest sensor calibration data and security patches. The traditional approach of physically visiting the device to perform these updates would be time-consuming, costly, and impractical, particularly if the device is situated in a remote or inaccessible area. By enabling SSH access to the device and connecting it to the AWS cloud, these updates can be performed remotely and securely. Furthermore, any critical issues that arise with the device can be addressed remotely, allowing for quick troubleshooting and restoration of functionality. This results in a significant reduction in operational costs and increased efficiency, while also improving security.
Setting up SSH access to your IoT devices in AWS involves several key steps. First, you will need to ensure that the IoT devices have SSH installed and properly configured. This typically involves installing the SSH server software, generating an SSH key pair, and configuring the SSH server to accept connections. Next, you will need to configure your AWS environment to allow SSH connections to your IoT devices. This will typically involve creating a security group that allows inbound SSH traffic on port 22, associating the security group with the devices. It is critical to restrict access to the security group to only authorized IP addresses. For enhanced security, you can utilize AWS Identity and Access Management (IAM) roles to manage access to your resources, and use key-based authentication. Using key-based authentication instead of passwords is highly recommended.
When configuring your IoT devices, it's important to follow best practices. Enable firewall rules that restrict access to only necessary ports, disable unused services and remove unnecessary software. Regularly update the operating system and SSH software to patch security vulnerabilities. Implement intrusion detection and prevention systems (IDS/IPS) to monitor network traffic for malicious activity and take proactive measures to mitigate threats. You can leverage AWS services such as Amazon CloudWatch to monitor logs and metrics, and set up alerts for unusual activity. Automating these steps can reduce the administrative overhead of managing large fleets of devices, and also improve the efficiency of your operations.
Let's delve deeper into some practical considerations. One of the most critical aspects of securing SSH connections is using strong authentication. Password-based authentication is highly discouraged due to the risk of brute-force attacks. Instead, implement key-based authentication, which uses a private key on your client machine and a corresponding public key on the IoT device. This method is significantly more secure. Furthermore, regularly rotate your SSH keys to mitigate the impact of any potential key compromise. Consider using a passphrase to protect your private key. A passphrase acts as an additional layer of security. It protects your private key. In the event your private key is compromised, a potential attacker would still need to know your passphrase in order to access your IoT devices.
The security group acts as a virtual firewall, controlling the traffic that is allowed to reach your IoT devices. Configure the security group to only allow SSH traffic on port 22 from specific IP addresses or IP address ranges that are authorized to access your devices. Avoid opening up the security group to the world by using "0.0.0.0/0" which allows all traffic. This greatly reduces the attack surface of your devices. Consider using network access control lists (ACLs) for additional layer of network security. Using both security groups and NACLs can further enhance the security of your AWS environment.
Regularly monitor your devices, analyze logs, and review security configurations. AWS provides robust logging and monitoring services such as Amazon CloudWatch, which can be used to track events, monitor performance, and generate alerts. Configure CloudWatch to monitor SSH login attempts, system errors, and other security-related events. Regularly review these logs and alerts to identify any suspicious activity. Also, implement a vulnerability scanning process to identify security weaknesses. AWS provides tools and services to assist with vulnerability management. These include Amazon Inspector and Amazon Security Hub. Proactive vulnerability management helps you identify and remediate potential vulnerabilities before they can be exploited.
Consider the case of a smart agriculture system, designed to optimize crop yields by monitoring soil conditions, weather data, and plant health. The system comprises a network of IoT sensors deployed across a large farm. Each sensor collects data and transmits it to a central server hosted in AWS. SSH access is critical in this scenario for several reasons: It allows for remote firmware updates. Remote diagnostics are also essential for addressing any issues, and enable secure data retrieval. Without SSH, the management of this complex system would be extremely difficult, if not impossible. The ability to securely and reliably manage the devices ensures the system's operational efficiency and data integrity.
One of the most common challenges when implementing SSH access to IoT devices is dealing with devices behind Network Address Translation (NAT). NAT is frequently used in home and cellular networks, and it can obscure the public IP address of the IoT device. This makes it difficult to directly connect to the device from the internet. One solution to this problem is to use a reverse SSH tunnel. A reverse SSH tunnel allows the IoT device to initiate a connection to a server in the cloud, and then you can connect to the device through the server. Another approach is to use a VPN (Virtual Private Network). A VPN creates a secure tunnel between your devices and the cloud, enabling you to access the devices as if they were on the same local network. Another consideration is the choice of SSH clients. A variety of SSH clients are available for different operating systems. Popular choices include OpenSSH (available on Linux and macOS), PuTTY (for Windows), and mobile apps for Android and iOS. Choosing the right client is important and should align with your workflow.
Another crucial consideration is the management of SSH keys. For large deployments, managing SSH keys can become a complex undertaking. Consider using an SSH key management system, such as HashiCorp Vault or AWS Secrets Manager, to store and manage SSH keys securely. These systems provide features such as key rotation, access control, and auditing. Remember to securely store your private keys and never share them with unauthorized individuals or store them in public repositories.
In addition to security considerations, it is also important to consider the performance implications of using SSH. SSH adds some overhead to the communication process due to its encryption and authentication mechanisms. In resource-constrained environments such as many IoT devices, this overhead can be a concern. Optimize your SSH configuration to minimize performance impact. For example, you can disable unnecessary features such as X11 forwarding and compression. Carefully evaluate the trade-off between security and performance, and choose the configuration that best meets your needs. Consider using alternative protocols such as MQTT for specific types of communications. Using MQTT can offer a lightweight and efficient alternative, particularly for sensor data transmission.
Another important consideration is the operating system of the IoT device. The operating system on the device plays a critical role in its security posture. Many IoT devices run custom or embedded operating systems, which can have different security features and vulnerabilities. Ensure the operating system is regularly updated with security patches. Monitor for any known vulnerabilities specific to the operating system. Consider using security-focused operating systems designed for IoT devices, such as Zephyr or FreeRTOS. These operating systems are designed with security in mind and provide features such as secure boot and secure over-the-air (OTA) updates. The security of the underlying operating system is a crucial factor.
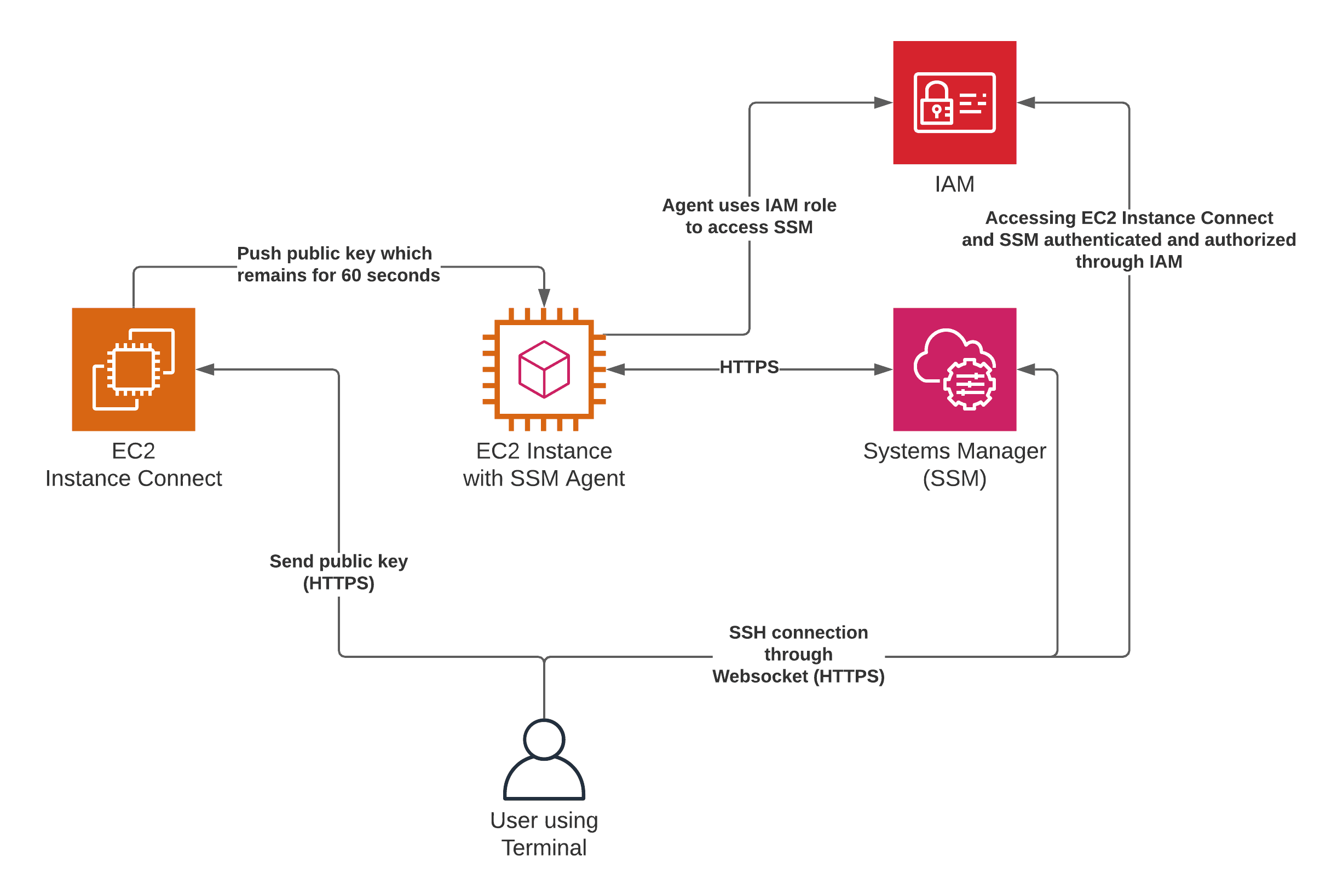
AWS offers a variety of services that can simplify the process of managing SSH access to your IoT devices. AWS Systems Manager (SSM) can be used to remotely manage your instances, including IoT devices. SSM provides features such as command execution, patching, and configuration management. Using SSM can reduce the need for direct SSH access, improving security and simplifying management. Another option is AWS IoT Device Management, which provides a centralized console for managing your IoT devices, including device provisioning, security, and software updates. This provides a more holistic approach to managing your fleet of devices.
In summary, SSH access to IoT devices in AWS offers a powerful combination of security, flexibility, and scalability. By implementing best practices and leveraging the AWS ecosystem, you can create a secure and efficient management solution for your IoT devices. Ensure a secure configuration by using strong authentication methods, following security group configurations, and regular monitoring and auditing, along with a well-defined update and patching strategy. This approach enhances security and maintainability.
Lets illustrate this with a real-world case study. Consider a smart city project deploying thousands of air quality sensors throughout the city. These sensors transmit data to AWS for real-time monitoring and analysis. SSH is crucial for: securely updating the sensor's firmware, troubleshooting any issues remotely, and performing system maintenance. Using SSH enables efficient data management and enables proactive system management. Proper configurations and security measures are implemented to protect the network. This case study underscores the necessity of SSH in enabling secure and efficient IoT device management in AWS, showcasing its practical application.
In conclusion, while the challenges associated with securing and managing IoT devices are undeniable, the combination of SSH and AWS provides a robust framework for addressing these challenges. By adopting a proactive approach to security, implementing best practices, and leveraging the power of AWS services, you can build a secure and reliable IoT infrastructure that empowers you to connect, manage, and protect your devices effectively. The key to success lies in understanding the specific security risks associated with your deployment, implementing appropriate security controls, and continuously monitoring and improving your security posture.
In order to summarize this, the best way to protect your data is to implement these features: Always use key-based authentication. Configure security groups correctly, and monitor logs. Regularly update the OS and SSH software. Use intrusion detection systems. Consider using a VPN. Automate as many of these steps as you can, and regularly review your overall security approach. By taking these steps, you can achieve effective management and secure access for your devices.